Summary
Intility builds and delivers a multi-cloud IT platform as a service. Our goal is to make both established and emerging technologies available to our customers, as part of a fully managed, pre-integrated, and continuously evolving technology platform. We aim to “pave the road” to continuous integration and development of both traditional and cloud-first workloads, enabling companies to continuously improve their digital platforms and processes, thereby attaining, and maintaining competitive advantage. All companies on Intility have, by definition, migrated their workloads to the cloud.
Intility offers Azure management with two tiers.
- Azure Landing Zone
- Application Management
Managed Azure Landing Zone scales on subscriptions and includes policy management and consulting in Azure. For customers on a Managed Azure Landing Zone, defender for cloud is activated, where Intility assists with the review of security alerts and advises the customer on improvements, but the customer himself is responsible for implementing changes.
Application Management in Azure requires a managed Azure landing zone, and entails an end-to-end responsibility for the underlying application platform in Azure, regardless of whether it runs on PaaS or IaaS. In these scenarios, Intility will be responsible for setup, operation, support, change management and monitoring of the platform. For modern workloads with continuous development (DevOps), this requires a high degree of coordination and interaction between Intility as supplier and the Customer in regard to changes that needs to be performed.
Intility delivers services in Azure based on Infrastructure as Code (IaC). If Intility will manage a production environment, but not a development environment, Intility can share the code used for setting up production, so that the Customer or a third party can set up an almost identical environment for development and testing. In the future, work is being done to ensure that the templates for services Intility creates and operates for customers can be shared via a repo so that customers themselves can retrieve and use these to set up infrastructure that is in accordance with Intility's standard and management.
Where the customer wants to be responsible for the underlying platform and IaC, Intility's role will be limited to the Managed Landing Zone, alternatively Intility will assit with advice and monitoring.
There are pros and cons when utilizing public clouds, as well as a need for strategic choices to be aligned with public cloud adoption. This document explains how Intility can serve in all aspects of utilizing public clouds and gives a description of Intilitys comprehensive management solution for Microsoft Azure.
Please note that the Azure platform and the corresponding management offering, is continuously under review and will be updated to reflect the current service offering as well as new functionality in Azure. Cost increases may occur to account for added functionality, for both management and consumption costs. This description will thus be updated to reflect the current offering at the time of reading.
Intility Managed Azure
Intility provides a comprehensive management solution for any customer initiative in Azure and offers Azure management with two tiers.
- Azure Landing Zone
- Application Management
Intility Managed Landing Zone (Optional)
Azure Landing Zone
Intility provides Managed Azure Landing Zone as the most fundamental management level in Azure.
Landing Zone is based on Microsoft Cloud Adoption Framework (CAF) Enterprise Scale Landing Zone.
An Azure Landing Zone is the output of a multi-subscription Azure environment based on strategies and processes for key areas: scale, security, networking, governance, and identity. The policies and processes defined for these areas are shared by all subscriptions, regardless of the underlying platform.
Intility provides a Managed Azure Landing Zone by delivering a set of processes and policies on the tenant and subscription layer based on best practices. Thus, tenant management and subscription management together are what constitutes an Intility Managed Landing Zone.
Azure Tenant Management
By default, two role groups are created in the customers Active directory catalog. They are: Reader, Contributor. In Azure AD two corresponding role groups are created. The Role groups are nested together as shown:
- Employee/user -> local role group -> Azure role group -> subscription
- Invited guest user third party -> Azure role group -> subscription
The implementation project will map and establish a baseline of users and group memberships. In production, self-service change is available through Intility portal.
Service includes:
- User management Internal, And guest users from partners.
- Role management and user assignments on subscription and resource groups.
- Managing Service accounts and application registrations.
- Integration of Active directory in data path on Azure resources.
Options:
- Privileged Identity management, Audit etc.
- Multi Factor Authentication (MFA).
- Conditional Access, and multi-level MFA
- Other custom integration of Azure Active Directory (AAD)
Azure plan, reseller agreement, admin agent
When the customer starts using Azure an Azure plan must be in place to gain access to Azure Resources. This can be activated by Intility.
In term of agreement, an active Microsoft Customer Agreement (MCA) must be signed directly with Microsoft and when onboarded to Intility the customer is invited to enter a Microsoft reseller agreement (Cloud Solution Provider) with Intility. The CSP agreement allows Intility to Buy Microsoft Licenses and Azure services on behalf of the customer. All services from Microsoft are then supported and billed from Intility.
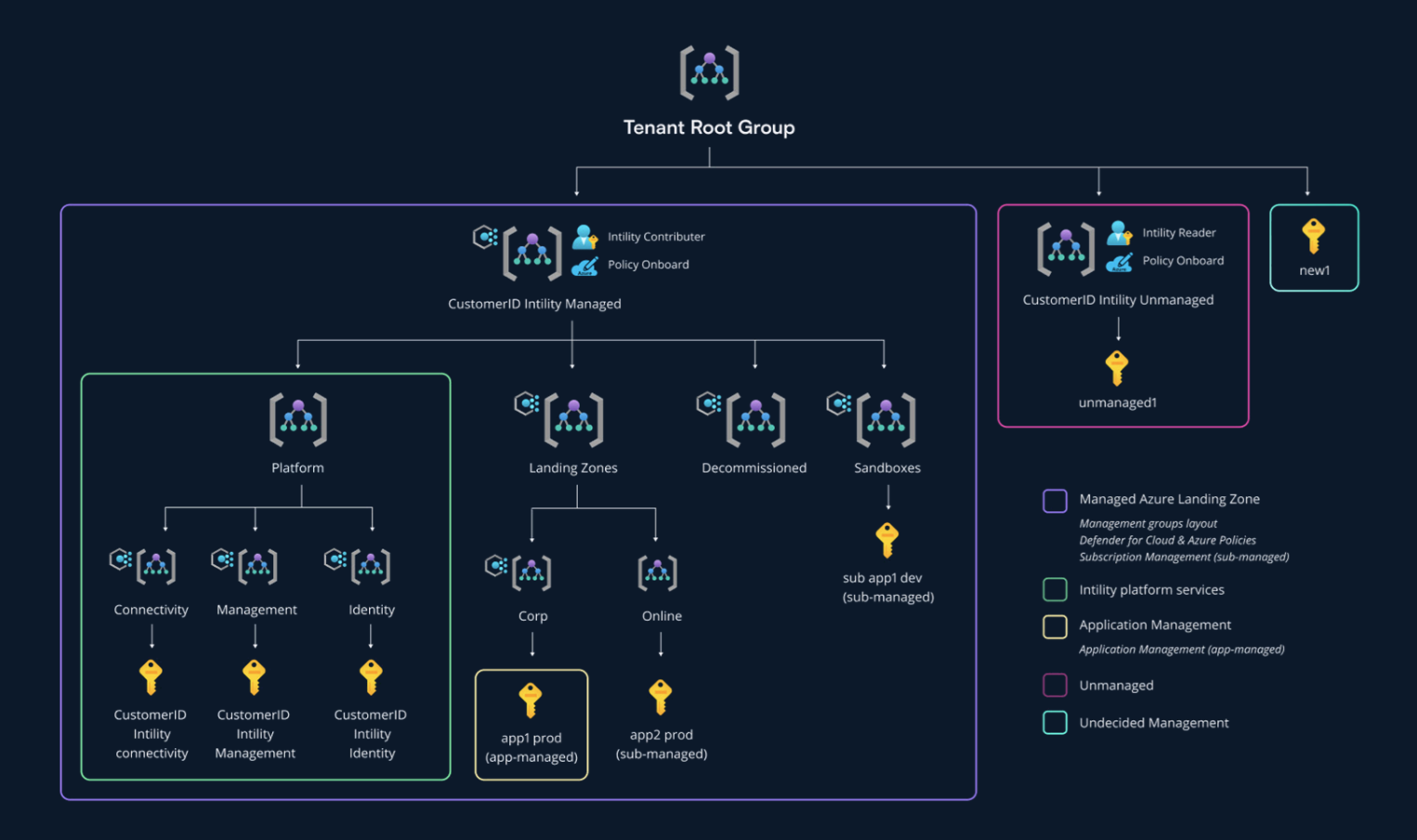
Management Groups
Intility deploys Management Groups in line with Microsoft Cloud Adoption Framework (CAF). The Management Group structure is illustrated below:
The Management Group structure is mainly divided into two; One management group for Intility Platform Services (Platform) and one for the customers application. Intility Platform Services contains of subscriptions and resources used by Intility, forexample network and logging.
The customers application are again divided into the following groups:
Corp: The
customer's resources which must only be available internally, and which must
only be accessible from the customer's network.
Online : Contains resources that can be available externally.
Decomissioned : Resources that are to be deleted at some point are placed here before final termination.
Sandbox: Resources used for R&D, testing, etc.
Azure Subscription Management
Managed subscriptions are the foundation for Intility Azure Management, which is activated per subscription.
A managed subscription has the following objectives:
1. Giving the customer an applied best practices framework in Azure. This especially applies if the customer has a mature IT organization and manages and runs the services and applications in the subscription themselves.
This reduces the time and money spent creating and maintaining an Azure governance model.
2. Making Intility consultancy services available, as well as reducing administrative overheads connected to such services.
A familiar framework and governance model are required for Intility to deliver consulting services. A pre-existing framework also saves a lot of time
3. Integrating the customer’s Azure Environment with the customer’s Intility environment.
Azure Direct Link is delivered as a service and requires Intility’s Azure networking baseline (a part of the Landing Zone) to be deployed to the Subscription.
4. Giving the customer access to Intility’s continuous development and improvement on Azure Management.
The Azure Landing Zone is continuously being improved.
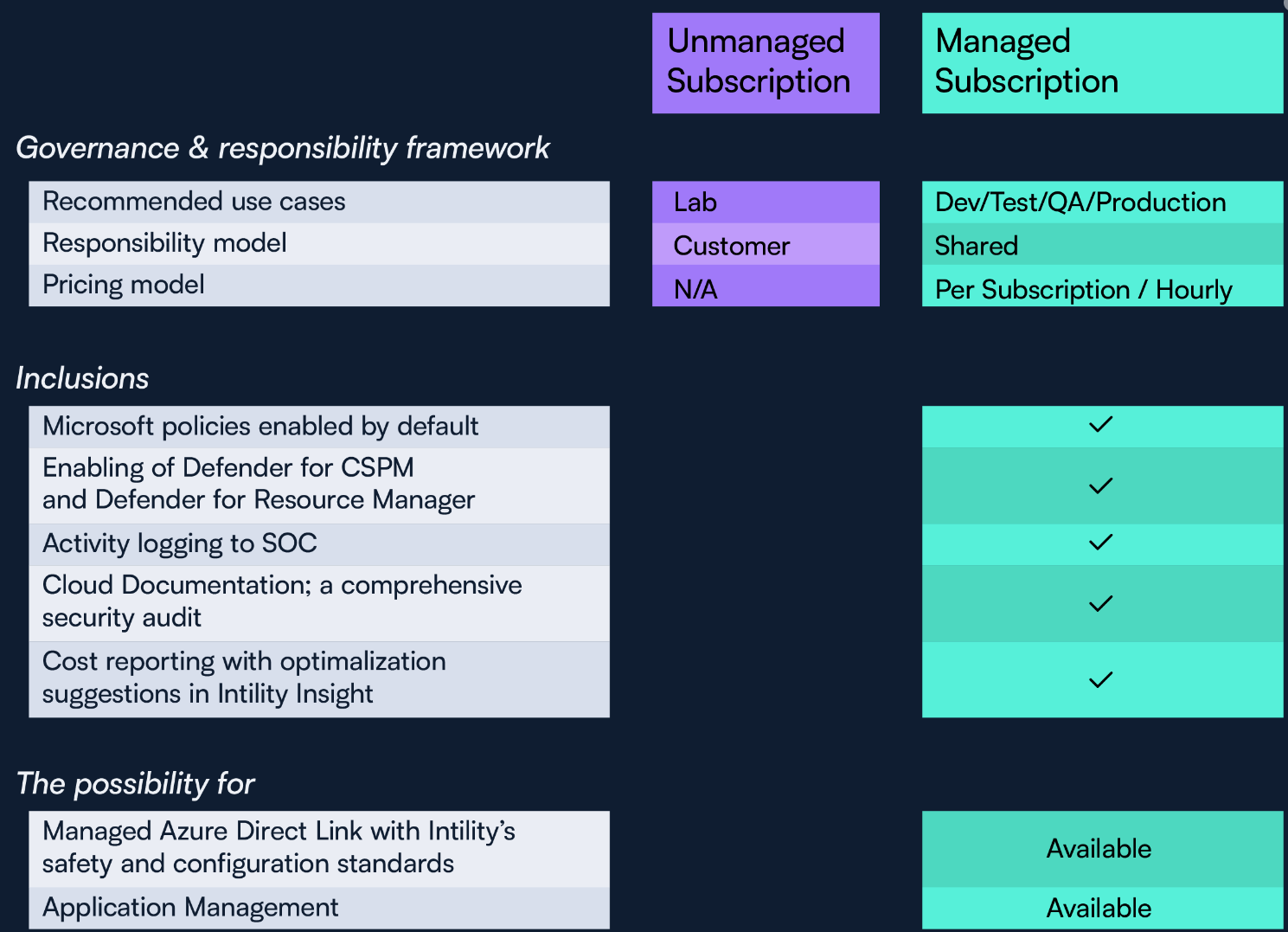
Managed Subscriptions are recommended for all subscriptions. These subscriptions give the following Shared Responsibility Model:
On the other hand, Subscriptions without Landing Zone come with zero involvement by Intility. Such subscriptions are useful for sandbox and lab environments. Unmanaged Subscriptions are not recommended for companies without a firm grasp of the scope and complexity of Azure management, regardless of the use case. On this tier, the customer assumes full responsibility for all aspects of the Subscription.
For the time being, a Managed Subscription includes the following services and opportunities. As it is a service in continuous development, changes and improvements to the service can be made on a regular basis.
- Microsoft policies enabled by default
- Enabling of Defender for Cloud Security Posture Management and Defender for Resource Manager
- Centralized activity logs to Intility SOC
- 24/7/365 security incident response from Intility SOC
- Cloud Documentation; a comprehensive security audit
- Cost reporting with optimalization suggestions in Intility Insight.
- The possibility for Managed Azure Direct Link with Intility’s safety and configuration standards.
- The possibility for Application Management
Microsoft policies enabled by default
Policies are enabled based on the security benchmarking standards from Centre for Internet Security (CIS), Microsoft Cloud Adoption Framework (CAF) and Intility best practices. Intility cannot force all standards for every customer but will recommend customers to review any non-compliant Resource with our technical or legal staff.
Managed Subscriptions are configured with Azure Security Centre standard edition by default. Customers will be charged for consumption costs related to Security Centre. As part of enabling Security Centre Intility also enables Azure Defender for customers with managed subscriptions. Azure Defender enables detection and response capabilities and provides a security layer against brute-force attacks and SQL injections.
Enabling of Defender for Cloud
Managed Subscriptions are configures with Defender Cloud Security Posture Management (Defender CSPM) and Defender for Resource Management as default, and customers will be invoiced for consume related to security center. These offerings will be delivered with management by Intility Security Operations Center which will be responsible for following up deviations and to take care of generated alarms.
Centralized activity logs to Intility SOC
Activity logs are being sent to Intility Security Operation Centers central log tool. This gives Intility the opportunity to create custom alarms as well as access logs in order to understand and track the activity and why the security incident occur.
Cloud Documentation; a comprehensive security audit
At any time, the customer can export a comprehensive document (“Cloud Documentation”) which includes relevant documentation about each resource, misconfigurations and potential security threats.
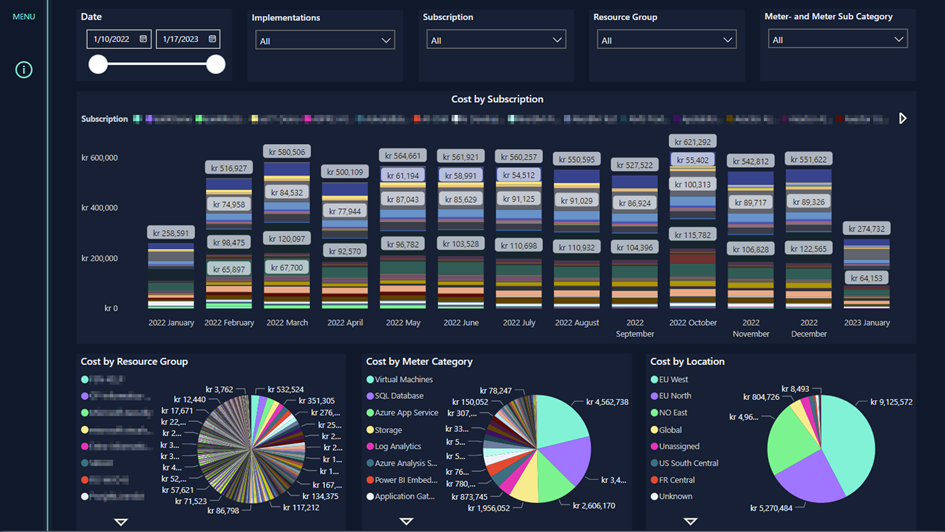
Cost reporting with optimalization suggestions in Intility Insight
Cost management can at first seem complicated when getting started in Azure. That is why a full overview of costs is made available as a report in Intility Insight together with other services from Intility.
The cost report for Azure contains several sub-reports which together presents a complete overview of consumed services in Azure. The various reports have the following purposes:
1) Provide a solid and total overview of the customer’s consumption in Azure as well as the related management fees. The overview is intended to explain the costs over time to uncover peaks,lows, and trends.
2) Costs by subscription and resource group. This report provides insight into costs distributed across different environments, systems, and applications over time.
3) The «Top 5 Usage Drivers» report shows the 5 biggest costs that run in Azure and their development over time. In addition, it is possible to identify the top 5 categories as well as the top 5 SKU or service types and filter between these.
4) If customers want a deeper insight into the various cost elements, a matrix has been made available that shows each individual category and any service in the selected subscription.
5) The Reserved Instance Advisor report provides suggestions for cost savings by looking at the number of VMs that have been running for the last 30 days and which are being paid with a “pay-as-you-go” pricing model. It also calculates what these VMs would have cost if these instances had been pre-paid over 1 or 3 years, as well as the amount of savings.
6) Map: Shows a geographical presentation of where services would run if that would be relevant. This view can, for instance, make it easy to identify the location of backups, network exit nodes, CDNs, and other relevant services.
7) Forecasting shows expected consumption for the next 30 days.
These reports are just a limited selection of the insight you will gain with cost management from Intility, and new reports are being developed on an ongoing basis.
The possibility for Azure Direct Link with Intilitys safety and configuration standards
Intility’s network policy baseline contains all necessary networking such as foundations for ExpressRoute, S2S VPN, security groups, operational tools, and access to core services. Connection to the customer’s Azure virtual network (VNet) is configured as “hub and spoke.” During Subscription enrolment, all automatic network openings will be removed (“zero trust”), to ensure that data is not accidentally exposed. VNet peering is applied, as well as Network Security Groups (NSG) to secure each service. VNet peering to the Intility tenant and onwards to the Intility Cloud is optional and the need for this is defined early in the planning phase.
The possibility for Application management in Azure
With Managed Azure Landing Zone, all resources and applications running in Managed Subscriptions can be managed by Intility, Managed Landing Zones is therefor a prerequisite for Application Management. Next chapter contains a more detailed description of Application Management.
Application management in Azure (Optional)
Intility provides application management in Azure as an end-to-end service for applications and workloads running in Azure. This service consists of both resource management and application management. Therefore, Application Management in Azure pricing scales with (1) Subscriptions and (2) the type and number of Resources running in the Subscriptions.
Application Management includes 24/7/365 support, application monitoring and automatic error correction, change management, client management, and coordination of third parties, continuous risk mitigation, and the establishment and maintenance of detailed documentation. A common data model for tools, monitoring and documentation ensures that compatibility overviews, log data, monitoring data, product data and knowledge articles can be used for predictive analysis and continuous improvement across the companies on the platform. This ensures stability, guaranteed availability, and high performance for the Customer's applications.
Application Management includes server-based applications, PaaS-based applications, client-based applications, and any combinations of these. The management portfolio consists of a wide range of applications, such as unique applications developed by the Customer or a third party, ISV (off-the-shelf) applications installed and configured on the Customer’s environment, or SaaS-applications delivered by various independent suppliers. Management, monitoring (where relevant) and documentation of dependencies between different applications and services, are included in responsibility from the Supplier as Single Point of Contact.
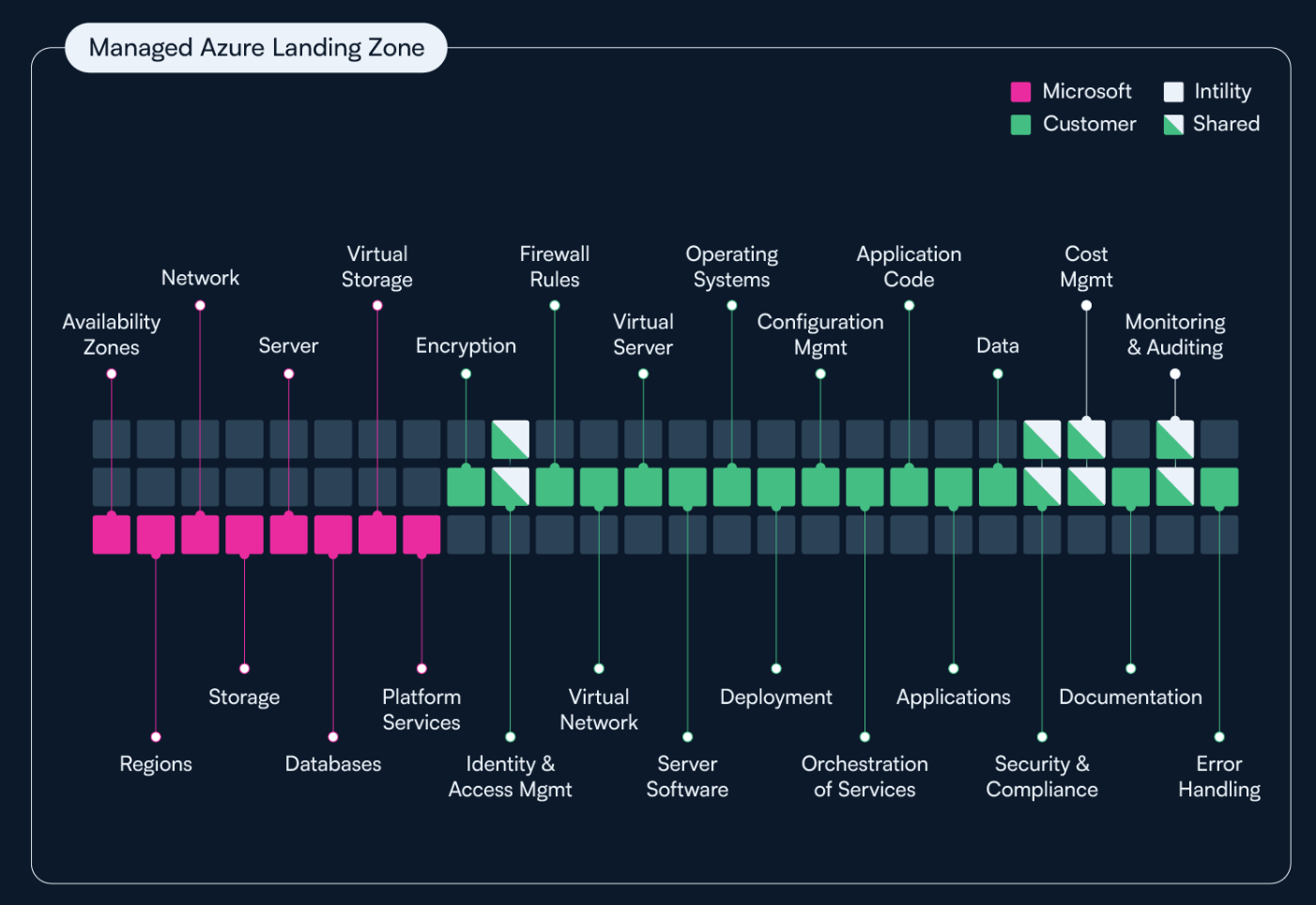
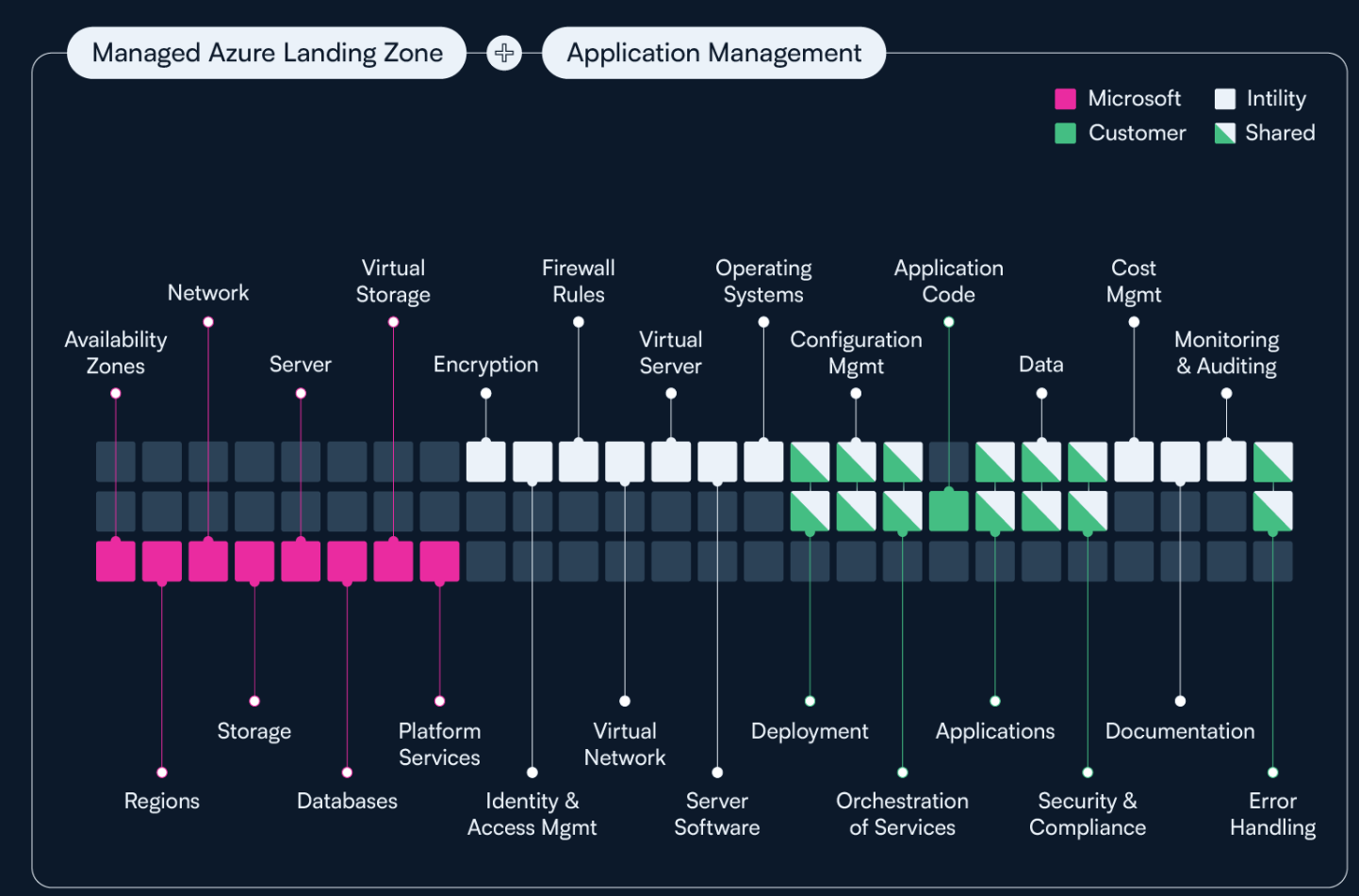
With Landing Zone and Application Management, the Shared Responsibility Model will be as illustrated below:
Application monitoring
Application monitoring provides the Supplier's monitoring division detailed and immediate insight in the event of an error and forms the main basis for proactive application operation. In most cases where there is an event of a breach of accessibility or other defined threshold values, an automatic error correction is implemented which is predefined and programmed for the given error. If the error is repeated or automatic error correction is not possible, an alarm is generated. Alarms are received and handled 24/7/365 by the Supplier's Operations Centre, which in close collaboration with the Supplier's application specialists works to continuously improve operational stability. This combination of automation and continuous improvement work leads to fewer error situations and reduced solution time in the event an error.
The application monitoring is based on the core system Dynatrace. Dynatrace is an agent-based tool that is installed on a server and automatically acquires data about the normal operating pattern of the infrastructure and application. This means that the product detects all processes running on a server and the agent is automatically instrumented, without the need for scripting or manual configurations.
Dynatrace is a multi-use tool which means that it supports several different technologies across the Supplier's cloud platform and Public Clouds such as Azure. This means that Dynatrace is used both for monitoring infrastructure and core technology such as VMWare, OpenShift, Citrix and ADC, in addition to monitoring both middleware such as various database technologies and web services, as well as monitoring the customer's applications.
The Supplier also gives the Customer the opportunity to gain full insight into their own monitoring by giving system owners, developers or other superusers access to the Dynatrace interface. This is an additional service that includes both the license, infrastructure and management that provides a unique insight into your own system crib.
Application support and alert management
The provider acts as a Single Point of Contact for application errors and changes.
Errors in the application layer or underlying infrastructure will, generally, be caught automatically by the application monitoring and, if automatic error correction is not successful, generate alarms to Intilitys operations centre. Error correction is performed based on error correction routines described in the knowledge article associated with the specific alarm. If the manual error correction routine solves the problem, the case will be closed. If the measures proposed in the article do not remedy the error, the alarm will be categorized, prioritized, and escalated to an application specialist.
The Supplier’s application specialists possess in-depth knowledge about the application platform and the Customer’s applications. They have access to a variety of tools for troubleshooting and analysing the relationships between application, database, operating system, virtualization, network, and hardware. If neither defined error correction routines nor further troubleshooting leads anywhere, the issue is escalated to the application provider. This will also be the case if the error turns out to be inside the application itself.
If neither defined error correction routines nor further troubleshooting leads anywhere, the issue is escalated to the application provider. This will also be the case if the error turns out to be inside the application itself. In the meantime, the Supplier will consider different options to implement a workaround, so that the users are able to use the service. The Supplier assumes responsibility for correcting the error and identifying the root cause of repeating errors, with support from the Customer’s application provider.
Repeating errors are identified either by the Supplier’s operations center, application monitoring specialists or Service Level Manager in the Application Operation team. When identifying an error, a preliminary root cause analysis will be performed before the issue is categorized and escalated for implementation of improvement measures in the infrastructure or application layer. Once the root cause is identified it will be resolved to avoid similar incidents in the future. This includes configuration of any relevant new monitors, improvement of existing monitors, and the update of any related knowledge article.
Handling of application providers and third party suppliers
Relevant customer-, supplier- and other third-party roles are documented for all Implementations in extension to a migration or establishment on the Supplier's platform. This entails full control in the event of errors or changes and highlights who is responsible for each part of a system's supply chain. User inquiries are directed to the Supplier's ServiceDesk, which, in accordance with the documentation, corrects, escalates, and coordinates. The roles can be edited by the Customer directly in the Portal, so that the Supplier always has up-to-date information on which resources are to be contacted for various purposes.
Security
This chapter describes the organizational and technical information security measures that protect the Intility platform and outlines how Intility focus on security.
Information security and compliance have a central role in the delivery and development of Intilitys services. Correct utilization, operations and management of security technology combined with a continuous focus on information security and compliance defines a level of quality that meets requirements in strictly regulated industries.
Security Management Systems
Intilitys information security management system (ISMS) aims to reduce the risk of incidents that may threaten the confidentiality, integrity and availability of information and data in its services. The system is based on the Cloud Controls Matrix (CCM) developed by the Cloud Security Alliance. The CCM framework consist of cloud specific security measures aligns and mapped with best practice frameworks such as PCI-DSS, ISO 27001 og COBIT.
Intilitys ISMS are described in two comprehensive reports issued annually and certified by an independent auditor (currently PwC).
The reports provide audit assurance and insight into Intility's security and privacy-related measures and controls. This year's ISAE 3402 report has been expanded to 129 controls from last year's 100.
The ISAE 3402 type 2 report provides audit assurance and insight into Intility's information security measures and controls. The report covers the following control areas:
- Intility platform management
- Managed customer environments
- Manged customer endpoints
- Managed Azure/Office 365
The ISAE 3000 type 2 report provides audit assurance for Intility's privacy and data protection measures and controls relevant for our role as a data processor under the GDPR. The report covers the following control areas:
- Privacy management
- Use, store and dispose
- Disclosure
- Monitoring and enforcement
- Data security
Risk Management
Risk management and risk assessments are carried out regularly with meetings and workshops involving stakeholders and key technical personnel. In these meetings risks are identified, analysed, evaluated and documented. Measures that are identified to reduce individual risks are escalated to service owners and/or department managers. Intility has established guidelines that indicates when, who and how Intility must carry out risk assessments.
Audit and Security testing
Intilitys ISAE reports documents that controls have been prepared and implemented in line with recognized frameworks for internal control, information security and privacy. The ISAE report is distributed to Intilitys customers via the Intility Portal and shows the degree of compliance in e.g. GDPR and the ICT regulation.
Intility carries out monthly security and penetration tests in collaboration with external security companies. These simulates cyber attacks against Intility, makes security assessments and tries to identify and exploit any vulnerabilities in the infrastructure to confirm and improve security. In addition to this, Intility carries out a minimum of annual security and penetration tests against the supplier's infrastructure.
Confidentiality
In regard to information security and to secure both customers' and Intilitys information, all employees have signed a non-disclosure agreement. This is included as part of all employment contracts. The confidentiality declaration is part of the internal information security policy and imposes a duty of confidentiality.
In the event of a security breach
Intility regularly reports on security incidents that affect the customer. These are available through the Intility portal. Customer-specific security reports are also prepared if the Customer is exposed to security incidents.
Advice and Assistance
The security department deals with issues relating information security in meetings on a daily basis and acts as an advisory partner towards Intilitys customers. Examples of current issues that the security department collaborates with Intilitys customers on is: customer-specific routines to ensure a sufficient degree of information security, customer-specific conditions regarding compliance with various regulatory legal requirements and specific technical requirements for the customer's setup.
Security Operations Center
Intility Security Operations Center (SOC) is a specialized department with dedicated resources that exclusively works to identify and reduce risks of unauthorized access and to protect the underlying platform.
SOC is central to Intilitys operational and technical work to ensure confidentiality, integrity and availability of the information that Intility manages.
SOC monitors and acts on security incidents 24/7/365 and works closely with security vendors to mitigate incidents, notify involved parties and coordinate error correction work.
Web Application Security
As organizations increasingly adopt web applications, the risk of attacks and exploitation of weaknesses in the application layer also increases. With countless combinations of commercially available web applications that are distributed to companies, the threat picture also changes as the complexity of the web applications increases.
The standard architecture for webbased services is that they are publised via a reverse proxy (ADC) solution. Intility offers setup and management of Application Gateway, Front Door or Cloudflare. A more comprehensive description of Cloudflare is shared by request.
Management of SSL Certificates
SSL certificates for internet services are issued to a domain to prove the authenticity of the service and are an essential part of SSL technology. The certificate authority signs and guarantees the origin of the web service, and it is automatically validated against approved root certificates already installed in the browser.
Intility has extensive experience in managing SSL certificates and, with the help of Citrix Application Delivery Controller, has achieved an A+ score on SSL Labs' (https://ssllabs.com) test of this type of certificate configuration.
Intility uses Digicert as the Certificate Authority (CA), and the certificates have a validity of one year before they need to be renewed. If the customer already owns a certificate from another issuer, it can be used until its expiration and replaced with Digicert certificates upon renewal.
Intility monitors both the expiration date and status of SSL certificates. For certificates purchased through Digicert, Intility has control over the expiration date regardless of the location. For certificates issued by other providers, such as Buypass, an SCOM agent is used for monitoring. This requires the certificate to be placed in the Windows Certificate Store. The customer will also have full visibility of all certificates purchased through Intility, where they are installed, which domain they are associated with, and the expiration date in Intility Insight.
When Intility receives a notification that a certificate is about to expire, the designated contact person is alerted, and upon confirmation, Intility renews the certificate. If the customer owns certificates from a different issuer than Digicert, Intility seeks to replace them with Digicert certificates whenever possible during the renewal process.
Intility offers the following certificates through Digicert: Standard SSL certificate, Multi-Domain certificate, Wildcard SSL certificate, Code Signing Certificate and PKI certificate.
Strategy for implementation
Implementation options
There are several ways to create and manage resources in Microsoft Azure. Resources can be created and managed either through the graphic interface in the Azure portal, by using PowerShell scripts, through Azure Command-Line Interface (Azure CLI), or by utilizing Infrastructure as Code (IaC) such as Azure Resource Manager (ARM), Bicep, Terraform or similar.
Infrastructure as code
Intility strives to deploy all resources in Azure as code. Utilizing infrastructure as code triggers many benefits such as repeatability, easier to scale, security, versioning of infrastructure, as well as an effective way of restoring or redeploying platforms to a new region. Intility has IaC templates in different frameworks depending on the resource and are mainly focused on Azure Resource Manager (ARM) templates or Bicep, although some resources are deployed by using Terraform.
Managing resources as code does create some challenges as it removes the possibilities to manually override configurations, and it requires a single source of truth for the current platform state. The customer and third parties must therefore develop a deployment plan together with Intility in terms of who is responsible for performing deployments, configuration changes etc.
Intility are building a library consisting of Infrastructure as Code templates based on our own and Microsofts best practices for configuration of services. Intility utilizes this library for deployments to Azure, and regularly reviews and updates this both with configuration updates, as well as including new services.
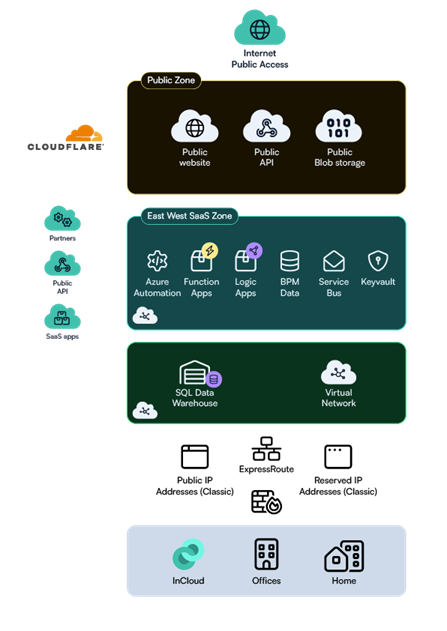
Zone model
Best practice network-level security has been around for decades. And modern security design assumes that the threat actor has broken the network perimeter, making Identity the primary.
A good and effective zone model is still recommended as it effectively reduces the vectors that can be used as a source of brute-force, DDoS, etc.
The figure below illustrates a zone model with the following attributes:
- Internet
- Frontend
- Backend
- East west SAAS integration
- Intility Incloud integration
Security policies
Azure Security Benchmark initiative is a collection of policies that ensures that azure resources deployed are secure and reliable. The initiative currently has 203 policies. Intility is evaluating the policies. Enabling and updating policies as needed and monitor resources deployed for compliance. Changing application configuration to meet current or new policies are not included in the service. Other initiatives are currently being evaluated.
Defender for cloud
Microsoft Defender for Cloud is a Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) for all your Azure resources. Defender includes a set of agents that:
- Continually assesses your security posture so you can track new security opportunities and precisely report on the progress of your security efforts.
- Secures your workloads with step-by-step actions that protect your workloads from known security risks.
- Defends your workloads in real-time so you can react immediately and prevent security events from developing.
Defender is deployed on all managed resources included in a managed applications architecture. Configuration alerts from defender are evaluated and mitigated as needed in the deployment project.
Alerts from defender can be routed to the customer for further processing and evaluation. Configuration management or can be monitored in Azure security dashboards.
Logging
Activity logging is turned on and data is stored in log analytics inside the customer subscription.
Activity logging enables 24/7 insights and enables event management and investigation into root cause to incidents etc.
Loging also enables an evidence base for compliance auditing.
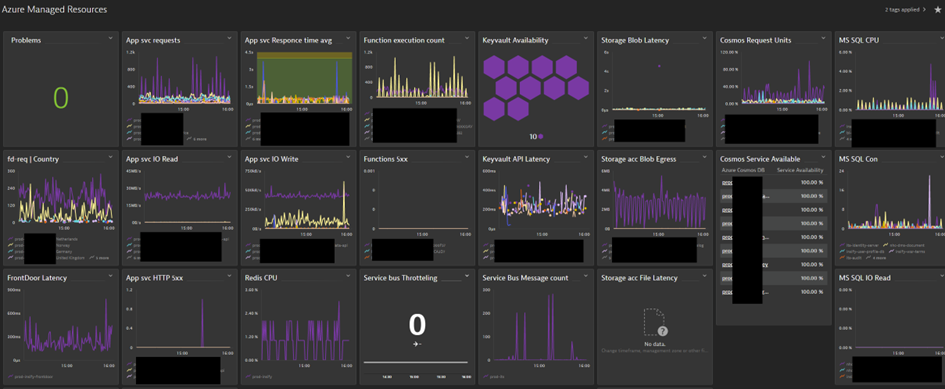
Monitoring
Implementation project includes by default:
- Metrics are enabled that monitor availability and performance of the most common resource types in the subscription by Dynatrace
- Basic end user synthetic monitoring (URL availability by dynatrace)
- Application performance dashboard template in Dynatrace.
Deeper and more detailed monitoring are available by request, as a billable expansion to the included monitoring. Current offer includes:
Intility action group for azure monitors that send alerts to Intilitys monitoring platform
End user synthetic monitoring can be expanded to include multi step processes.
Query based alerting: When logging exceptions using application insights. An alert can be configured to fire based on events from a scheduled log query.
Data backup
All resources that contain data are identified and a backup restore plan is implemented. We normally implement data retention and backup using features embedded in the resource with a retention policy as close to 7 days - 4 weeks – 3 months. Where available. We also make sure that the backup sett is available in a different datacentre region in case of disaster recovery.
Configuration backup
As resources are deployed using Infrastructure As Code (IAC) the configuration is backed up using a code repository. Intility uses Gitlab to maintain IAC. In cases where there is no IAC code. An export of current configuration is saved to the repository as ARM templates.
Disaster recovery options and plans
Disaster recovery plans that match business expectations is essential. As standard Intility suggests expanding the IAC code to be able to deploy to two different regions. Along with data backup It will form the basis for a DR plan. The plan needs to be tested and updated on regular intervals. Typical restore scenarios lasts 1-2 days using this method.
Incloud Network Integration
Managed Azure Network | VNet
Managed Azure virtual network (VNet) is configured in a “hub and spoke” model, where the customer's VNet (spoke) is connected to a hub through VNet peering. The hub acts as a gateway for all spokes and ensures network traffic between Microsoft Azure and the Intility Cloud. VNets that need to communicate with Intility Cloud have to follow Intility standards when it comes to IP allocation. Requirements for IP addresses have to be confirmed early in the planning phase.
When a Virtual Network is deployed, the VNet will be locked down (“zero trust”) with either Network Security Groups or Application Security Groups, to ensure that data is not accidentally exposed. VNet peering will also be applied.
Managed Azure Direct Link | VPN
Azure Virtual Private Network (VPN) is Intility’s standard solution for network connection between the Intility Platform and Microsoft Azure. VPN offers maximum flexibility and can be set up to all Azure datacenters, either directly from the customer site or from Intility’s network integration hub resources. The standard solution is configured with full encryption on all traffic and cross-datacenter tunnels to ensure redundancy and uptime.
Azure Direct Link | VPN is available only on Managed Subscriptions with Managed Azure Landing Zone.
Managed Azure Direct Link | ExpressRoute
Azure ExpressRoute offers a dedicated and private cloud connection between the Intility Cloud and selected Azure datacenters and regions, including Norway East and West Europe. The solution enables high-capacity data transfers over a fixed route with stable latency. ExpressRoute also offers an extra layer of security as the traffic is not exposed over the public internet.
Azure Direct Link | ExpressRoute is available only on Managed Subscriptions with Managed Azure Landing Zone.
Documentation and configuration management
All resource groups and resources that is managed by Intility have two tags associated.
- IntilityImplementationGUID = <guid> Identifies the corresponding Application the resources belong to. Governance, contact roles, monitoring, FAQ, and articles are then added at det application level.
- IntilityManaged = true Signifies that this resource is managed and monitored by Intility.
Intility is automatically mapping resources to Applications using the tags. The applications are then visualized as the center piece in our tools that links to all relevant information.
Azure Implementation Project
Azure implementation projects follow a lot of the same steps and processes as a normal establishment project on Intilitys platform. The different phases and milestones may vary depending on the scope of the project, deadlines, and deliverables, but this description provides a general overview of the main activities and dependencies throughout the project. An Azure project can be structured differently depending on the scope and requirements, and the phases described here are a general description.
Mapping
In this phase the main objective is to get a clear understanding of the projects scope, and map out all resources that will be affected, as well as activities, milestones, deadlines, and dependencies.
Another important part of the mapping phase consists of sorting out stakeholders, governance model, management level and performing a gap analysis of current and desired configuration state. This part of the project will be performed in close collaboration between Intility, the customer and other relevant third parties.
Plan and design
The plan and design phase are based on the information uncovered in the mapping process and key deliverables from this face is an overall architecture of the proposed solution including:
- Disaster recovery planning
- High-availability considerations
- Network and sone model
- Policy mgmt., including security policies
- Identity and access mgmt.
- Infrastructure as Code procedures
- Partner plan
The output of this phase is what defines all the subscriptions under Intility management and is what creates the foundation for the Intility Managed Landing Zone.
Create and migrate
During this phase the results of the mapping, plan and design will be deployed. This will preferably be done through Infrastructure as Code, where templates are available. During this phase, Intility will establish:
- Subscriptions in a structure as agreed in the previous phase
- DevOps pipeline
- Documentation
- Tags
- Resources: Monitoring, Backup, Disaster recovery plans
This phase also includes a data migration from the current setup to the new platform.
Testing and validation
Testing and validation of the new platform will be done in close collaboration with the customers super users, third party vendors and resources from Intility to validate the new solution. In addition to testing the solution, other deliverables should also be tested such as DR plans, HA setup and monitoring, as well as validating the documentation created during the project.
For a more thorough description of the test phase please see appendix 4.
Go-live and approval
The last phase concerns the closing activities for the project and is often marked by a handover meeting from the project team to the customer. Other activities conducted are project review and approval, billing, project backlog or future projects enabled by the transition.
(A more detailed project plan i available on request)
Appendix
Microsoft Azure
Azure is Microsofts public cloud solution, providing a range of different cloud services such as compute, storage, AI, networking, DevOps, and a lot more. These services are available across multiple regions. The services offered are delivered as:
- Saas (Software as a Service) – such as Office 365 or Azure Machine Learning Studio
- PaaS (Platform as a Service) – such as Azure SQL or Azure Kubernetes Service
- IaaS (Infrastructure as a Service) – such as Virtual Machines and storage
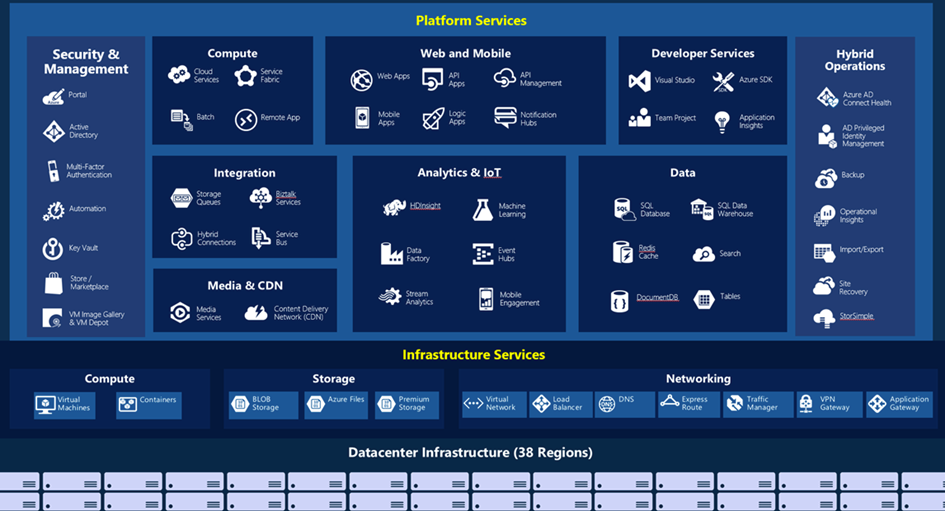
Azure terminology
Intility has developed a governance model which serves as the blueprint for any Azure initiative. Based on the customer’s organizational structure and access policies, the blueprint may be customized at the Tenant or Subscription levels.
An Azure Resource may have one or more Tags and exists in a Resource Group in a Subscription in a Tenant. These constructs are the foundation for Intility’s Azure governance framework.
Hyperscaler: Large companies providing public cloud offerings, such as Microsoft Azure, Amazon Web Services and Google Cloud Platform.
Tenant: Top-level framework for the customer’s infrastructure; that which distinguishes the customer from other companies on Azure. Most companies have only one Tenant. Tenant enrolment (Admin Agent) is a prerequisite for Azure Subscription management and allows Intility to perform configuration at the tenant level.
Subscription: All resources within a Subscription are on the same invoice. Most companies will have multiple Subscriptions to designate each to an application, a project, or a division within the organization. Azure management tier is assigned at the Subscription level, and applies to the Subscription itself, and all Resources in it. Subscription is the upper-most level in terms of access.
Azure Landing Zone: An Azure Landing Zone is the output of strategic choices shared for all subscriptions that accounts for scale, security, governance, identity, and networking. This enables application migration, modernization, and innovation at enterprise scale. This approach considers all platform resources that are used to support customers application portfolio. Landing Zones are divided in two different types: Platform landing zone and Application landing zone:
- Platform landing zones are focused on centralized key services delivered as consolidated services for multiple applications.
- Application landing zones are one or more subscriptions deployed as an environment for an application or workload.
Resource Group: A Resource Group is a logical collection of resources in Azure. A Resource, for example a storage account, can only reside in one Resource Group at any given moment. Resource Groups and are fundamental parts of governance and access control plans.
Resource: A Resource is an asset or configuration item. Managed Services typically scale per resource, as does Application Management.
Tag: Tags extend beyond Resource Groups and are used to quickly identify resources and/or Resource Groups, e.g., department, cost center, etc. Intility apply a set of default Tags and advise customers on an internal tagging policy.
Shared Responsibility Model: A shared responsibility model for operations accounts for the responsibilities of each party. Responsibilities vary for unmanaged subscriptions, managed landing zones, and resource and application management in Azure. The color-coded charts show the respective responsibilities of Microsoft, Intility, and the customer (alternatively a third party commissioned by the customer).
Considerations on moving to public cloud
There are several key elements that should be considered with regards to migrating to public cloud, or to keep running critical applications in a public cloud. When used correctly, hyperscale cloud platforms such as Microsoft Azure can open new opportunities, speed up development processes, and shorten time to market. There are however challenges in adopting and capitalizing on public cloud adoption that should be considered.
When not to use public cloud
Public clouds should be used for modern architectures, and not for retrofitting legacy systems. A virtual machine has the same tenets on both Azure and Incloud, and little is gained by rehosting one to Azure (“lift-and-shift”), especially compared to the effort needed to do it right in terms of backup, disaster recovery, networking, and security. This is contrary to most early (and many still ongoing) hyperscale cloud initiatives, which tend to be based on the assertion that there are massive costs waiting to be saved by migrating everything to hyperscale. Lifting-and-shifting always-on, non-scalable workloads does not cut costs.
There are of course use cases when migrating a VM would make sense, such as consolidating the components of a latency sensitive application in the same physical location as other application components. The key point is that major changes in existing applications should be done for a reason, with a clear goal, and a long-term benefit. Simply put, moving to a hyperscale cloud without capitalizing on new and available technology platforms will not provide the solutions and benefits companies often seek by moving to the cloud.
When to use public cloud
It is when you build new systems, or re-factor or re-architect existing applications, preferably with the goal of preparing it for long-term continuous development, that progress is made. In such scenarios, public clouds offer some complementary functionality to Incloud.
- When working with continuous integration and development, automation and self-service is key. If you new versions daily and your application auto-scales, you will appreciate the full-stack programmability of Azure.
- Most non-VM, non-SaaS workloads are, and will be, container based, itself an offering nonunique to hyperscale, and available both on Incloud and Azure. However, Azure also offers unique services which give clear advantages without necessarily increasing costs.
- Azure data and analytics services represent a particularly useful suite of such services, which are easily integrated with data sources on Incloud, other services on Azure, and PowerBI.
- When geography is important for the availability of your systems the possibility of geo-replication globally is an advantage with hyperscale clouds such as Azure.
- Applications built on new technologies, lighter workloads such as serverless functions, event handling, and event-based architecture, are well suited to hyperscale clouds.
What to consider when hyperscaling
- Incloud offers a multi-tenant, pre-configured security platform including high availability, disaster recovery, DDoS protection, and more. Intility will help Managed Azure customers obtain the same, high level of security. It should be noted, however, that copying the features of the Incloud Security Platform comes at a considerable cost of entry.
- The overall complexity of the platform will increase. Most operational and security considerations will still need to be made. Operating systems still need management. Networks still need to be configured and secured. In short, moving from Incloud to Azure without Intility Managed Azure, the customer is assuming many responsibilities and tasks which has not been previously taken. Get acquainted with the shared responsibility model corresponding to the different management levels offered.
- Hyperscale clouds are easy to get started with. This is great when launching a project, but creates complexity in terms of access management, administration rights, security, and cost considerations, especially when a system goes from development to production. Make sure that considerations and strategies for these areas are part of the design from the beginning to avoid potential issues.
- Compared to a non-hyperscale scenario, costs will most likely increase if not properly governed, and they will probably not decrease significantly. Cost optimization starts with the right architecture for the right workload. Intility Managed Azure gives you the tooling, but the customer is ultimately responsible for the services and plans chosen by its developers.
- Be proactive in staying compliant with GDPR and any other laws and regulations you are subject to. Make sure to risk assess all cloud providers and enter data processor agreements as necessary.
- Consider the team responsible for the solutions. The team must be knowledgeable about the platform and technology stack on which the solutions are built. As an Intility customer the team may consist not only of internal employees and consultants, but also Intilitys technical experts and advisors. Customers should build internal development teams rather than primarily being reliant on consultants, and to leverage Intility’s expertise on both platform and application portfolio as part of the team.
Governance tasks to consider
- Landing zone
- Order and create new subscriptions
- Cost control
- Reserved instances
- Network and Zone model
- Micro service and integrated service documentation
- Configuration management
- IAC
- IAM
- Security configuration and tools
- Backup and disaster recovery plans